How Many Steps Are in the Opsec Process
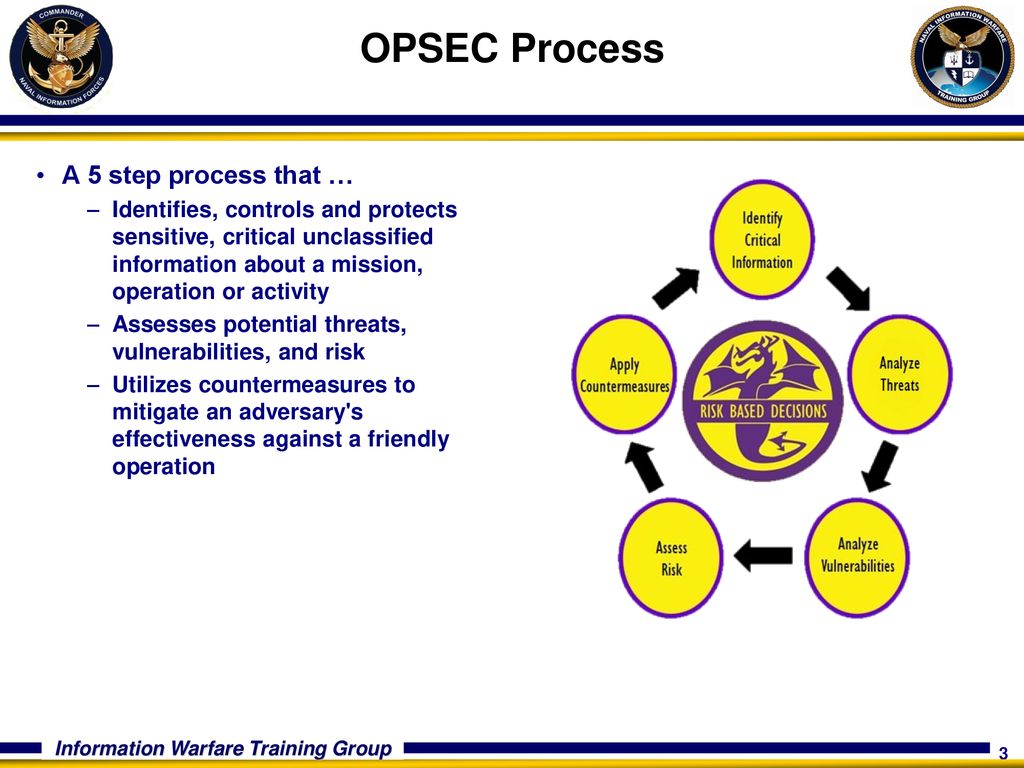
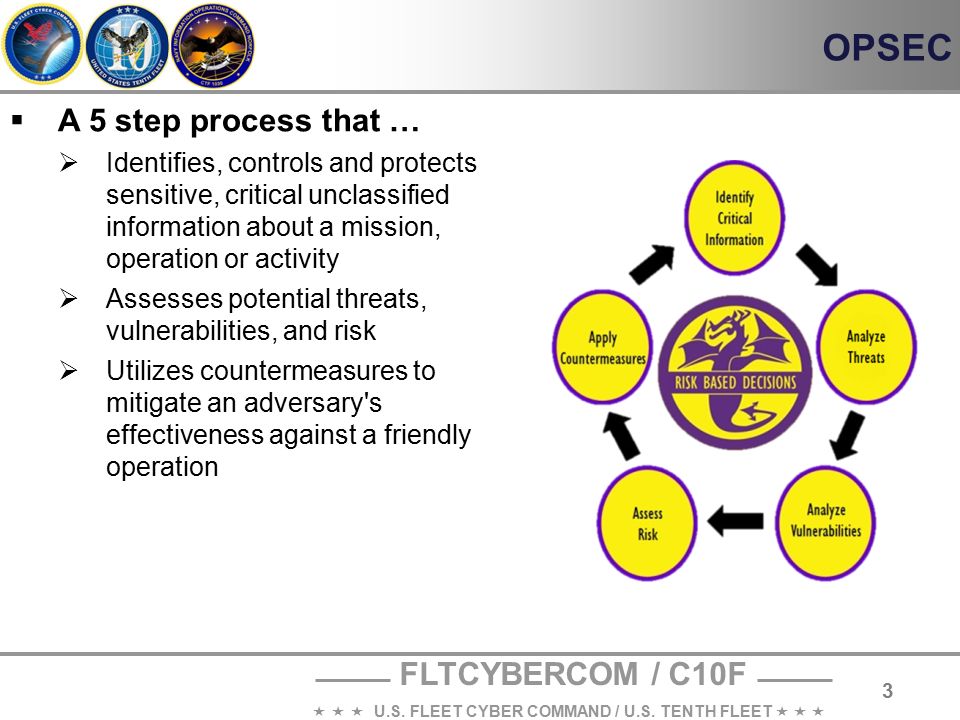
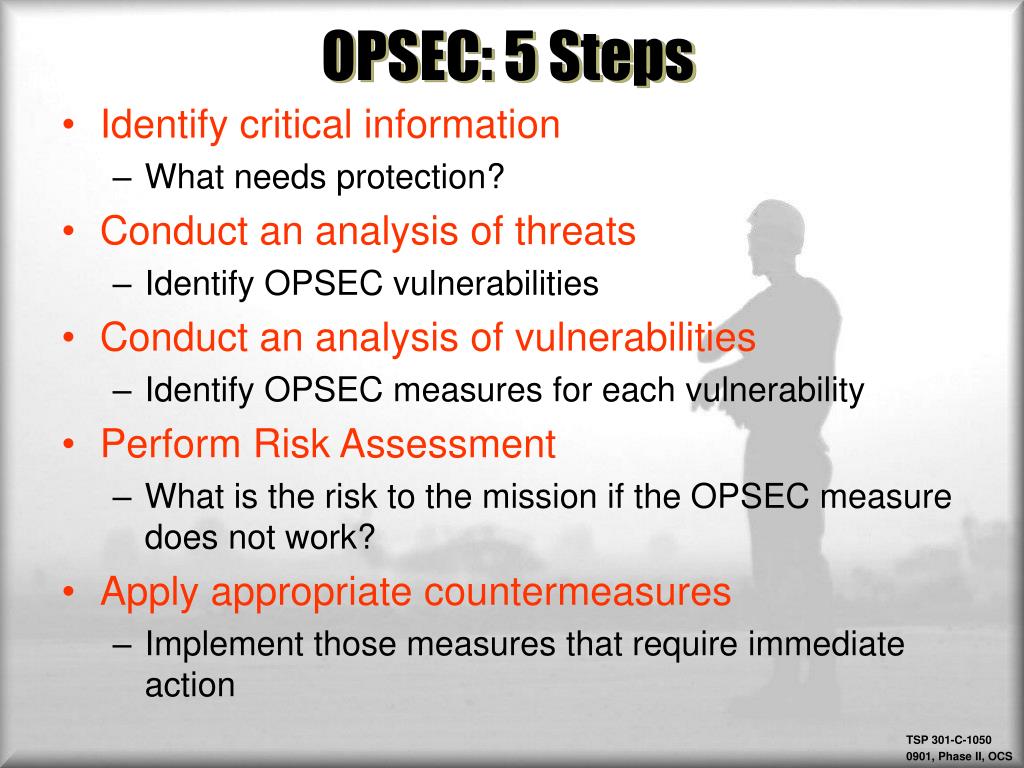
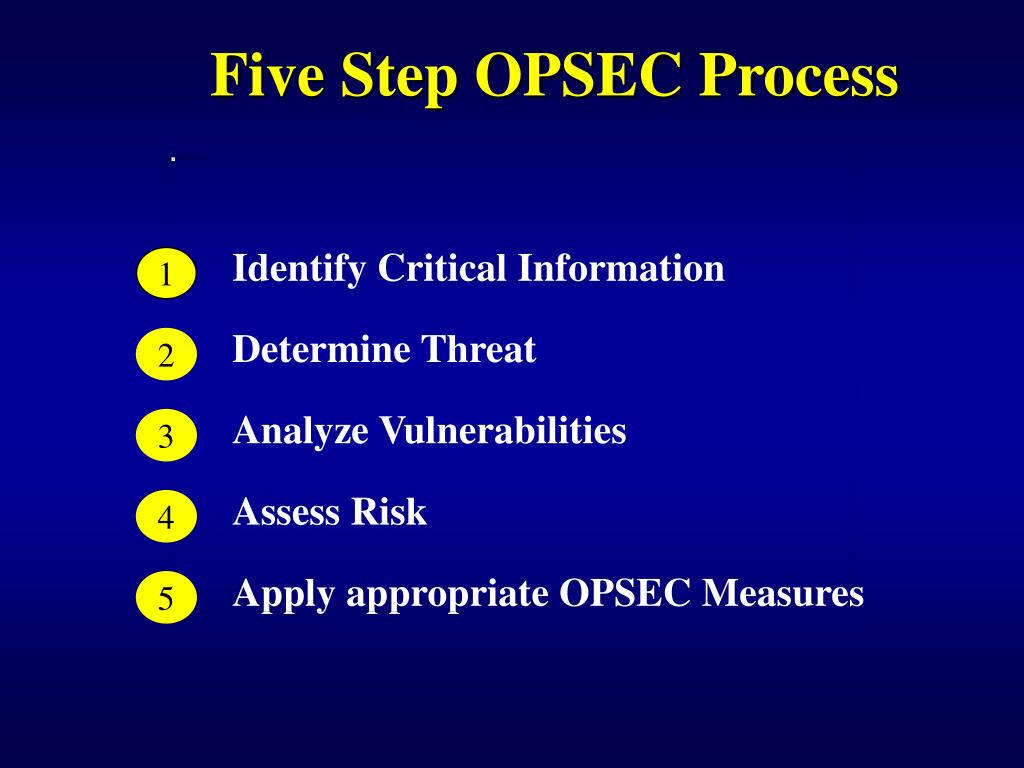
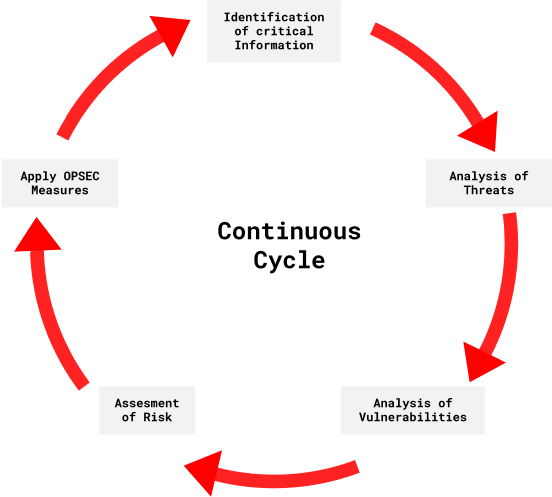
1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures. OPSEC analysis of vulnerabilities.

Opsec Process Glossary Course Map Mute Voice Transcript Opsec Circle Opsec Is Designed To Protect The Mission Determine How Adversaries Could Collect Information Regarding A Specific Operation Activity Or Project And Implement Countermeasures
Identifying critical and sensitive data.

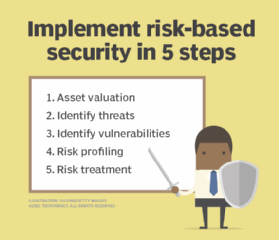
. What are the 5 steps of opsec. What are the 5 steps of the OPSEC process. Identify your sensitive data including your product research intellectual property financial statements customer information and employee information.
1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures. Thesesteps provide a framework for the systematic process necessary to identify. Making an OPSEC plan.
Identification of critical information. Military has established a five-step process by which organizations can assess their data and. The OPSEC Five-Step Process consists of.
1 Identify Critical Information 2 Analyze Threats 3 Analyze Vulnerabilities 4 Assess Risk 5 Apply Countermeasures. Step 5 Apply The Countermeasures. Its a process.
The OPSEC process involves five steps. A method of denying critical information to an adversary. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures.
The OPSEC Process consists of five interrelated steps. Start studying OPSEC Process Five Steps. Poster - Always Use.
Operations Security Family Guide. It is a methodology designed to guide the user through a series of steps to identify critical information and OPSEC indicators and develop. And the reason many of you are probably here step 5.
OPSEC Applications Applying the OPSEC Process OPSEC is beneficial for all levels in an organization Contingency operations can be compromised if OPSEC is NOT applied. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures. 1 identification of critical information 2 analysis of threats 3 analysis of vulnerabilities 4 assessment of risk and 5 application of appropriate countermeasures.
This will be the data you will need to focus your resources on protecting. Identification of Critical Information. Application of Appropriate Countermeasures.
The military has five basic steps to proper OPSEC and theyre just as useful in the civilian world especially with the proliferation of tech that makes leaks and security breaches more common. The OPSEC process is most effective when fully integrated into all planning and operational processes. The process involves five steps.
Operations Security OPSEC Operations Security is the systematic and proven process by which potential adversaries can be denied information about capabilities and intentions by identifying controlling and protecting generally unclassified evidence of the planning and execution of sensitive activities. The OPSEC process involves five steps. So what is the last step in the OPSEC process.
What are the 5 steps of opsec. The 5 Steps of OPSEC The OPSEC 5-Step Process provides. The OPSEC process consists of Five Steps which can apply to any plan operation program project or activity.
Assess OPSEC critical information. Any step in the OPSEC process may need to be revisited at any time. OPSEC is a process of identifying analyzing and controlling critical information indicating friendly actions associated with military operations and other activities.
OPSEC Fundamentals Course TEXT ONLY VERSION Module 3. Learn vocabulary terms and more with flashcards games and other study tools. Developing and implementing countermeasures.
The processes involved in operational security can be neatly categorized into five steps. OPSEC guide that provides commanders a method to incorporate the OPSEC process into daily activities exercises and mission planning to assist Navy and Marine Corps commands afloat and ashore in practicing and employing OPSEC. The OPSEC process involves five steps.
OPSEC isnt just a set of rules that tells you what you should or shouldnt say. The OPSEC process involves five steps. You need to begin by determining what data if acquired or accessed by an adversary would cause harm to your organization.
A holistic picture a systematic process for mission success and an analytical methodology for assessing critical information. What is OPSEC is concerned with. As stated above the five steps of the OPSEC process are.
The OPSEC process is most effective when fully integrated into all planning and operational processes. Navy Warfare Library publications must be made readily available to all users and other. Identify the responsibilities for all OPSEC actions in your plans It is extremely important for your family to follow the OPSEC process Overview of.
This can often be one of the more time-consuming steps so be sure to set enough time aside in advance to see what steps youll need to make in order to ensure youre covered on as many bases as possible. OPSEC assessment of risk. The OPSEC process involves five steps.
How many steps are in OPSEC process. A five-step process to identify control and protect critical information and analyze.
Command Indoctrination Operations Security Dd Mmm Yy Ppt Download

Opsec Process 17 Identifying Critical Information In The First Step Download Scientific Diagram

Operations Security Opsec For New Hires Ppt Download

Opsec Overview Glossary Course Map Mute Voice Transcript Opsec Circle The Opsec Process Includes The Following Steps Identification Of Critical Information Analysis Of Threat Analysis Of Vulnerabilities Assessment Of Risks Application Of Appropriate
What Is Opsec Operations Security

Secops Vs Opsec What S The Difference Bmc Software Blogs
Overall Classification Of This Briefing Is Unclassified Fouo Ppt Video Online Download

Military Discipline In Industrial Control Opsec Incibe Cert
What Is Opsec Operations Security

Operational Security Pcc Vii F Ppt Download
Ppt Implement Opsec Powerpoint Presentation Free Download Id 3523073

Operations Security Opsec For New Hires Ppt Download
Ppt Security Measures Iw 130 Powerpoint Presentation Free Download Id 243600

What Is Operational Security The Five Step Opsec Process Securitystudio
Online Privacy Through Opsec And Compartmentalization Part 3

Opsec Process 17 Identifying Critical Information In The First Step Download Scientific Diagram


Comments
Post a Comment